FreeRadius, LDAP and dynamic VLAN assignment
A long time ago I was interested in find out how I can use my installed FreeRadius to dynamically assign a VLAN based on an Actice Directory Group. First I’ll show my current setup:
- Microsoft Active Directory Domain Controller (Windows Server 2012 R2)
- FreeRadius (openSUSE Leap 15.3) – Installation instruction https://stangneth.com/2021/05/26/freeradius-on-opensuse/
- HP ProCurve 2810-24G
- Client (Windows 10 21H2)
Inhaltsverzeichnis
Active Directory group
After creating a local security group in Active Directory I assigned it to a User.
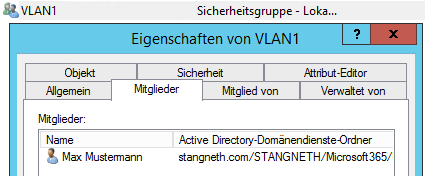
FreeRadius config
Edit the FreeRadius LDAP config in post-auth section to assign the VLAN based on this group.
vi /etc/raddb/sites-enabled/default
post-auth {
ldap
if (LDAP-Group == "VLAN1") {
update reply {
Tunnel-type = VLAN
Tunnel-medium-type = IEEE-802
Tunnel-Private-Group-Id = 1
}
}
elsif (LDAP-Group == "VLAN10") {
update reply {
Tunnel-type = VLAN
Tunnel-medium-type = IEEE-802
Tunnel-Private-Group-Id = 10
}
}
else {
update reply {
Tunnel-type = VLAN
Tunnel-medium-type = IEEE-802
Tunnel-Private-Group-Id = 666
}
}
Restart the FreeRadius Server and check if the auth is successfull.
rcradiusd restart
radtest -t mschap mustermann Start123 localhost 0 testing123
The result should us provide the Tunnel-Private-Group-Id.
Sent Access-Request Id 196 from 0.0.0.0:40761 to 127.0.0.1:1812 length 136
User-Name = „mustermann“
MS-CHAP-Password = „Start123“
NAS-IP-Address = 172.16.0.249
NAS-Port = 0
Message-Authenticator = 0x00
Cleartext-Password = „Start123“
MS-CHAP-Challenge = 0x6bd3b0199158881b
MS-CHAP-Response = 0x0001000000000000000
Received Access-Accept Id 196 from 127.0.0.1:1812 to 127.0.0.1:40761 length 99
MS-CHAP-MPPE-Keys = 0x0000000000000000f0fdf
MS-MPPE-Encryption-Policy = Encryption-Allowed
MS-MPPE-Encryption-Types = RC4-40or128-bit-Allowed
Tunnel-Type:0 = VLAN
Tunnel-Medium-Type:0 = IEEE-802
Tunnel-Private-Group-Id:0 = „1“
Switch Setup
Configure the radius server on the network switch. Be sure to setup the file /etc/raddb/clients.conf!
radius-server host 172.16.0.249 key secret12
Now we can enable eap-radius authentication for port-access. In this example for the port-range 1-10.
aaa authentication port-access eap-radius aaa port-access authenticator 1-10 aaa port-access authenticator active
On my Switch I have to be sure that GVRP is enabled. I’ve done this step within the menu.
- 2. Switch-Configuration
- 7. VLAN Menu…
- 1. VLAN Support
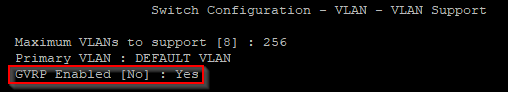
Also I have created a „Dead-VLAN“ with ID 666. This will be assigned if the client dont response with a valid username/password combination.
aaa port-access authenticator 1-10 unauth-vid 666
The ports can be monitored with the following command.
show port-access authenticator
Port Access Authenticator Status
Port-access authenticator activated [No] : Yes
Auths/ Unauth Untagged Tagged Cntrl
Port Guests Clients VLAN VLANs Port COS Dir
—- ——- ——– ——– —— ——— —–
2 1/0 0 10 No No both


Keine Kommentare zu FreeRadius, LDAP and dynamic VLAN assignment