FreeRadius on openSUSE
I changed my private wifi from WPA2 to WPA2-Enterprise. I no longer have to enter a one-time password, but can enable authentication using a username and password. For this scenario I’m using my MS Active Directory and a FreeRadius Server. Following you can find my configuration. Feel free to write comments or corrections in the comment-section.
Requirements
- Static IP
- /etc/hosts is showing to the Hostname /etc/HOSTNAME
- DNS Server is an Active Directory Domain Controller or can dissolve all Active Directory entries
- Chrony configured
Installation & configuration
- FreeRadius, Samba, Winbind und krb5 installation
zypper install freeradius-server freeradius-server-utils samba winbind krb5-user
- Edit Samba Config for Domain join
vi /etc/samba/smb.conf
[global] workgroup = STANGNETH realm = STANGNETH.COM security = ads idmap config * : backend = tdb idmap config * : range = 3000-7999 idmap config testing : backend = rid idmap config testing : range = 10000-999999 winbind use default domain = true winbind offline logon = false
vi /etc/nsswitch.conf
passwd: compat winbind group: compat winbind
vi /etc/krb5.conf
[realms]
STANGNETH.COM = {
kdc = server1.stangneth.com
admin_server = STANGNETH.COM
default_domain = STANGNETH.COM
}
[domain_realm]
.stangneth.com = STANGNETH.COM
stangneth.com = STANGNETH.COM
reboot
net ads join -U Administrator
Answer:
Using short domain name — TESTING
Joined ‚SMB‘ to dns domain “
No DNS domain configured for smb. Unable to perform DNS Update.
DNS update failed: NT_STATUS_INVALID_PARAMETER
systemctl restart smb winbind
Check connection to Active Directory
wbinfo -a mustermann%Passw0rd
Antwort:
plaintext password authentication succeeded
challenge/response password authentication succeeded
ntlm_auth --request-nt-key --domain=STANGNETH --username=mustermann --password=Passw0rd
Antwort:
NT_STATUS_OK: Success (0x0)
- Freeradius basic configuration
Edit certificates in section certificate_authority
vi /etc/raddb/certs/ca.cnf vi /etc/raddb/certs/server.cnf vi /etc/raddb/certs/client.cnf cd /etc/raddb/certs/ ./bootstrap
![[certificate authority]
c cun C yN ame
s C a C PI ovinceName
I ocaI i CyName
01 gani z a C i onName
emai e s s
c ame
NDS
S tad Cha gen
S t an gne th
adm@stangneth . com
"Stangneth Radius Certificate Authority"](http://blog.stangneth.com/wp-content/uploads/2021/05/image.png)
vi /etc/raddb/mods-available/ntlm_auth
require-membership-of is optional if you want to restrict access to a specific AD group
exec ntlm_auth {
wait = yes
program = "/usr/bin/ntlm_auth --request-nt-key --domain=STANGNETH --require-membership-of='$DOMAINNAME$DOMAINGROUP' --username=%{mschap:User-Name} --password=%{User-Password}"
}
vi /etc/raddb/mods-available/mschap
ntlm_auth = "/usr/bin/ntlm_auth --request-nt-key --domain=STANGNETH --username=%{%{Stripped-User-Name}:-%{%{User-Name}:-None}} --challenge=%{%{mschap:Challenge}:-00} --nt-response=%{%{mschap:NT-Response}:-00}"
vi /etc/raddb/mods-available/eap
default_eap_type = mschapv2
vi /etc/raddb/sites-enabled/default & vi /etc/raddb/sites-enabled/inner-tunnel
authenticate {
ntlm_auth
vi /etc/raddb/clients.conf
client Wifi-Gateway {
ipaddr = 172.16.0.139
secret = testing123
systemctl restart radiusd
Check Radius connection
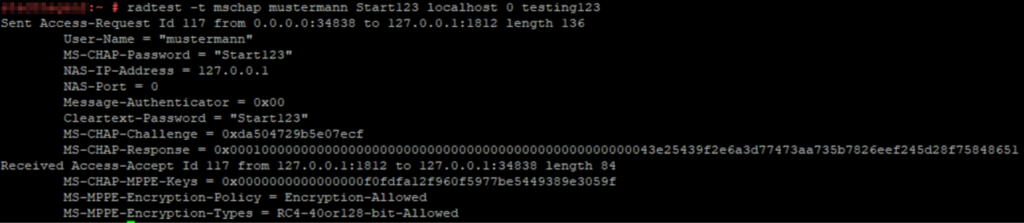
- LDAP connection
zypper install freeradius-server-ldap
vi /etc/raddb/mods-available/ldap
ldap {
server = 'server1.stangneth.com'
port = 389
identity = 'cn=ldap_user,cn=Users,dc=stangneth,dc=com'
password = Str0ng$ecret
base_dn = 'dc=stangneth,dc=com'
update {
control:Password-With-Header += 'userPassword'
control:NT-Password := 'ntPassword'
reply:Reply-Message := 'radiusReplyMessage'
reply:Tunnel-Type := 'radiusTunnelType'
reply:Tunnel-Medium-Type := 'radiusTunnelMediumType'
reply:Tunnel-Private-Group-ID := 'radiusTunnelPrivategroupId'
user {
base_dn = "${..base_dn}"
filter = "(sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})"
ln -s /etc/raddb/mods-available/ldap /etc/raddb/mods-enabled/
vi /etc/raddb//sites-available/default
Auth-Type LDAP {
ldap
}
authorize {
-ldap
ldap
if ((ok || updated) && User-Password) {
update {
control:Auth-Type := ldap
}
}
systemctl restart radiusd
Check LDAP connection
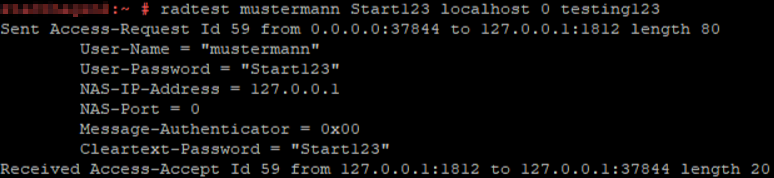
- LDAP group restriction
Check whether the user is a member of the Radius Group and additional query based on the NAS identifier if the group says he is allowed to use the „ENTERPRISE“ wifi.
vi /etc/raddb/sites-available/default
-ldap
ldap
if ((ok || updated) && User-Password) {
update {
control:Auth-Type := ldap
}
}
# Check if the user is member of the Group "RADIUS"
if (LDAP-Group == "CN=RADIUS,OU=Groups,OU=Microsoft365,OU=STANGNETH,DC=stangneth,DC=com") {
noop
} else {
reject
}
# WIFI ENTERPRISE
if (NAS-Identifier == "ENTERPRISE") {
if (LDAP-Group == "CN=WIFI-ENTERPRISE,OU=Groups,OU=Microsoft365,OU=STANGNETH,DC=stangneth,DC=com") {
noop
} else {
reject
}
}


Keine Kommentare zu FreeRadius on openSUSE