Unsere Dienstleistungen
Netzwerkoptimierung & Segmentierung
Optimieren Sie Ihr Netzwerk mit professioneller Segmentierung und Sicherheitsmaßnahmen.
UTM-Firewalls von Securepoint
Sichern Sie Ihr Unternehmen mit professionellen UTM-Firewalls und Netzwerk-Security.
E-Mail-Sicherheit & Spam-Filter
Schützen Sie Ihre E-Mails vor Spam, Phishing und Malware.
Monitoring
Überwachen Sie Ihre IT-Infrastruktur effizient und zuverlässig mit unseren maßgeschneiderten Monitoringlösungen.
Ticketsystem
Optimieren Sie Ihren Supportprozess mit einem leistungsstarken Ticketsystem auf Basis von Zammad.
Sicherheitschecks
Schützen Sie Ihr Netzwerk mit umfassenden Sicherheitsüberprüfungen und gezielten Optimierungen.
Netzwerkoptimierung & Segmentierung
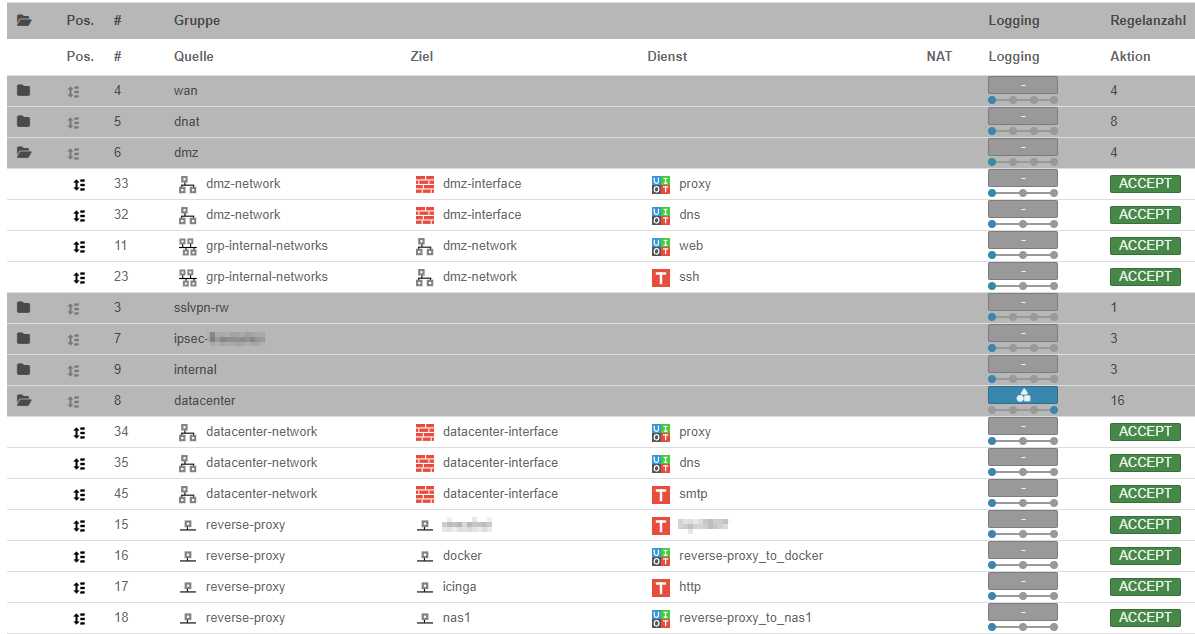
Ein gut durchdachtes Netzwerk ist das Rückgrat jeder modernen IT-Infrastruktur. Häufig sind Unternehmensnetzwerke jedoch unstrukturiert gewachsen und bieten somit ein hohes Risiko für Sicherheitslücken und Performance-Probleme.
Eine **Netzwerksegmentierung** bietet zahlreiche Vorteile: Sie verhindert unbefugten Zugriff, verbessert die Performance und reduziert die Angriffsfläche für Cyber-Bedrohungen. In einem segmentierten Netzwerk bleiben kritische Systeme geschützt, selbst wenn ein einzelner Client kompromittiert wird.
Warum Netzwerksegmentierung?
- Verbesserte Sicherheit: Trennen Sie sensible Systeme von alltäglichen Arbeitsgeräten und schützen Sie kritische Infrastruktur.
- Performance-Steigerung: Minimieren Sie unnötigen Netzwerkverkehr und verbessern Sie die Bandbreite für geschäftskritische Anwendungen.
- Bessere Kontrolle: Klare Richtlinien sorgen dafür, dass nur berechtigte Geräte auf spezifische Bereiche zugreifen können.
Unsere Lösungen
- Analyse & Planung: Wir untersuchen Ihr bestehendes Netzwerk und entwickeln eine maßgeschneiderte Segmentierungsstrategie.
- VLAN-Konfiguration: Durch den Einsatz von VLANs trennen wir Geräte logisch voneinander – beispielsweise Drucker, VoIP-Telefone, Server und Clients.
- Netzwerk-Härtung: Absicherung durch Firewalls, Access Control Lists (ACLs) und Zero-Trust-Strategien.
UTM-Firewalls & Securepoint

Als **Securepoint Operator Partner** biete ich Unternehmen eine umfassende Sicherheitslösung mit **UTM-Firewalls** (Unified Threat Management). Diese schützen Ihr Netzwerk vor Viren, Malware, Phishing und unbefugtem Zugriff – und das alles in einer einzigen, zentralen Lösung.
Warum Securepoint?
- Ganzheitlicher Schutz: Firewall, VPN, IDS/IPS, Web-Filter und Anti-Malware in einem System.
- Made in Germany: DSGVO-konform mit deutschem Support.
- Leistungsstarke Verwaltung: Zentrale Steuerung und Monitoring über das UTM-Interface.
Unsere Dienstleistungen
- Individuelle Firewall-Strategie: Maßgeschneiderte Konzepte für Ihr Unternehmen.
- VPN & sichere Zugriffe: Sichere Anbindung für Homeoffice & mobile Mitarbeiter.
- Regelmäßige Security-Updates: Wartung & Pflege für eine stets aktuelle Firewall.
E-Mail-Sicherheit & Spam-Filter
E-Mails sind eines der größten Einfallstore für Cyberangriffe. Phishing-Mails, Spam oder gezielte Spear-Phishing-Attacken können massive Schäden anrichten. Ich unterstütze Unternehmen dabei, ihre E-Mail-Kommunikation abzusichern und sensible Daten zu schützen.
Warum E-Mail-Sicherheit?
- Reduzierung von Spam: Automatische Filtermechanismen blockieren unerwünschte E-Mails.
- Schutz vor Phishing & Malware: Verdächtige E-Mails werden automatisch analysiert und abgefangen.
SPF, DKIM & DMARC – Wofür sind sie gut?
- SPF (Sender Policy Framework): Verhindert, dass Dritte in Ihrem Namen E-Mails versenden.
- DKIM (DomainKeys Identified Mail): Schützt Ihre Mails vor Manipulation durch digitale Signaturen.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): Kombiniert SPF & DKIM für höchste Sicherheit.
Unser Service
- Einrichtung & Optimierung: SPF, DKIM & DMARC-Konfiguration für Ihre Domain.
- Integration mit Firewall & Virenscanner: Mehrstufiger Schutz für Ihre gesamte Kommunikation.
- Überwachung & Anpassung: Regelmäßige Kontrolle, um Angriffsversuche zu minimieren.
Monitoring – Überwachung Ihrer IT-Infrastruktur
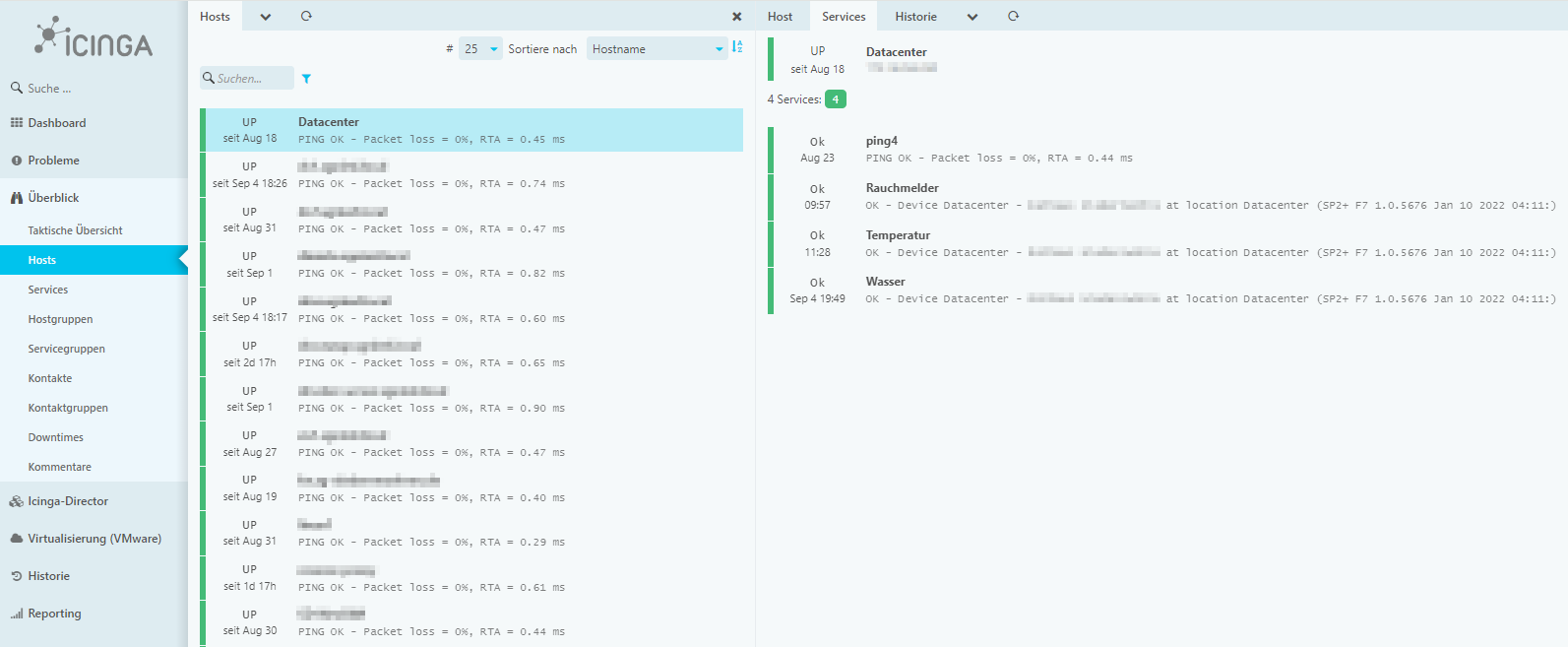
In der heutigen, hochvernetzten Welt ist eine stabile und sichere IT-Infrastruktur von entscheidender Bedeutung für den Erfolg eines Unternehmens. Mit unseren maßgeschneiderten Monitoringlösungen auf Basis von Icinga2 und openSUSE behalten Sie Ihre gesamte IT-Infrastruktur jederzeit im Blick. Wir bieten Ihnen eine umfassende Überwachungslösung, die auf die individuellen Anforderungen Ihres Unternehmens abgestimmt ist.
Warum Monitoring mit Icinga2?
Icinga2 ist ein leistungsstarkes Open-Source-Monitoring-Tool, das speziell entwickelt wurde, um komplexe IT-Umgebungen effizient und zuverlässig zu überwachen. Es ermöglicht eine präzise Überwachung von Netzwerken, Servern, Anwendungen und Diensten, sodass Sie jederzeit über den Zustand Ihrer Systeme informiert sind.
- Frühzeitige Problemidentifikation: Dank automatisierter Überwachung erkennen Sie potenzielle Probleme, bevor sie zu Ausfällen führen.
- Skalierbare Architektur: Icinga2 ist hoch skalierbar und kann problemlos an die Größe und Komplexität Ihrer IT-Umgebung angepasst werden.
- Flexibles Benachrichtigungssystem: Sie werden über Probleme in Echtzeit informiert – per E-Mail, SMS oder anderen Kommunikationskanälen.
- Grafische Visualisierung: Detaillierte Dashboards und Berichte bieten Ihnen klare Einblicke in die Leistung und Verfügbarkeit Ihrer Systeme.
- Integrierte Lösung: Icinga2 lässt sich nahtlos in bestehende IT-Umgebungen integrieren und bietet Schnittstellen zu anderen Systemen wie Ansible oder Docker.
Unser Service
Unsere Monitoringlösungen umfassen:
- Grundeinrichtung und Konfiguration: Wir übernehmen die komplette Einrichtung des Icinga2-Systems auf Basis von openSUSE. Dies beinhaltet die Anpassung an Ihre spezifischen Anforderungen.
- Inbetriebnahme erster Checks: Wir konfigurieren erste Checks, damit wichtige Komponenten Ihrer IT-Infrastruktur direkt überwacht werden.
- Einführung und Schulung: Wir schulen Sie und Ihr Team im Umgang mit Icinga2, sodass Sie zukünftig selbstständig Anpassungen und Erweiterungen vornehmen können.
Mit unseren Lösungen behalten Sie die volle Kontrolle über Ihre IT-Umgebung und minimieren gleichzeitig das Risiko von ungeplanten Ausfällen. Lassen Sie uns gemeinsam dafür sorgen, dass Ihre Systeme jederzeit optimal laufen.
Ticketsystem – Effizientes Supportmanagement mit Zammad
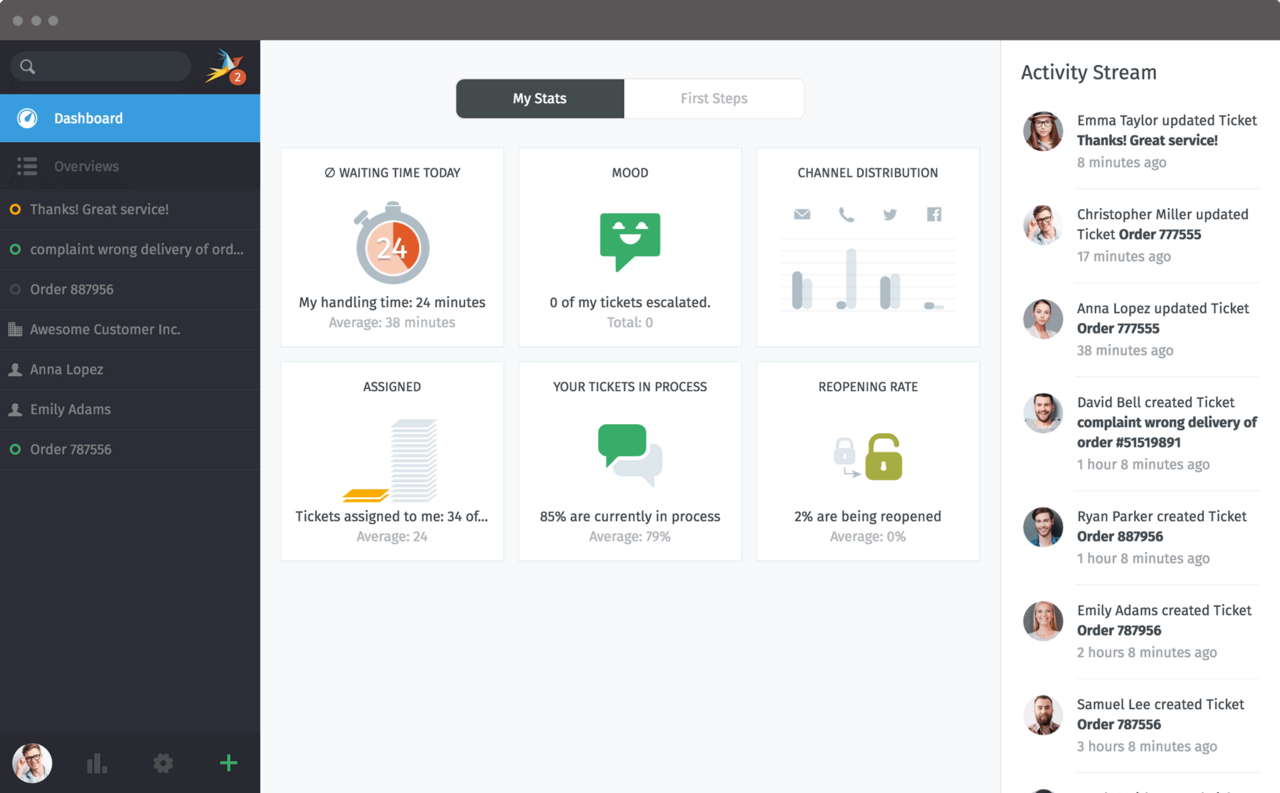
Zammad ist ein Open-Source-Ticketsystem, das speziell für die Verwaltung von Supportanfragen entwickelt wurde. Wir helfen Ihnen, Zammad optimal an die Bedürfnisse Ihres Unternehmens anzupassen.
Mit Zammad können Sie Kundenanfragen effizienter verwalten, die Kommunikation verbessern und interne Prozesse optimieren. Zu den wichtigsten Funktionen, die wir für Sie anpassen und konfigurieren, gehören:
- Multi-Channel-Support: Zammad integriert verschiedene Kommunikationskanäle wie E-Mail, Telefon, Chat und soziale Medien in eine zentrale Plattform, sodass alle Anfragen gebündelt bearbeitet werden können.
- Automatisierte Workflows: Wir richten flexible Automatisierungen ein, die wiederkehrende Aufgaben wie Eskalationen, Ticketzuweisungen und Benachrichtigungen übernehmen.
- Benutzerfreundliche Oberfläche: Zammad bietet eine intuitive Benutzeroberfläche, die sowohl für Support-Mitarbeiter als auch für Kunden leicht zugänglich ist.
- Self-Service Portal: Mit einem integrierten Self-Service-Portal und einer Wissensdatenbank können Ihre Kunden Antworten auf häufige Fragen eigenständig finden.
- Erweiterbare Integration: Wir integrieren Zammad in Ihre bestehenden Systeme, wie CRM- oder ERP-Software, um reibungslose Arbeitsabläufe sicherzustellen.
Unsere Dienstleistungen umfassen die vollständige Einrichtung, Anpassung und Einführung von Zammad in Ihrem Unternehmen. Wir stellen sicher, dass Ihre Supportprozesse effizient und auf Ihre speziellen Anforderungen zugeschnitten sind.
Sicherheitscheck – Netzwerksicherheit mit Greenbone
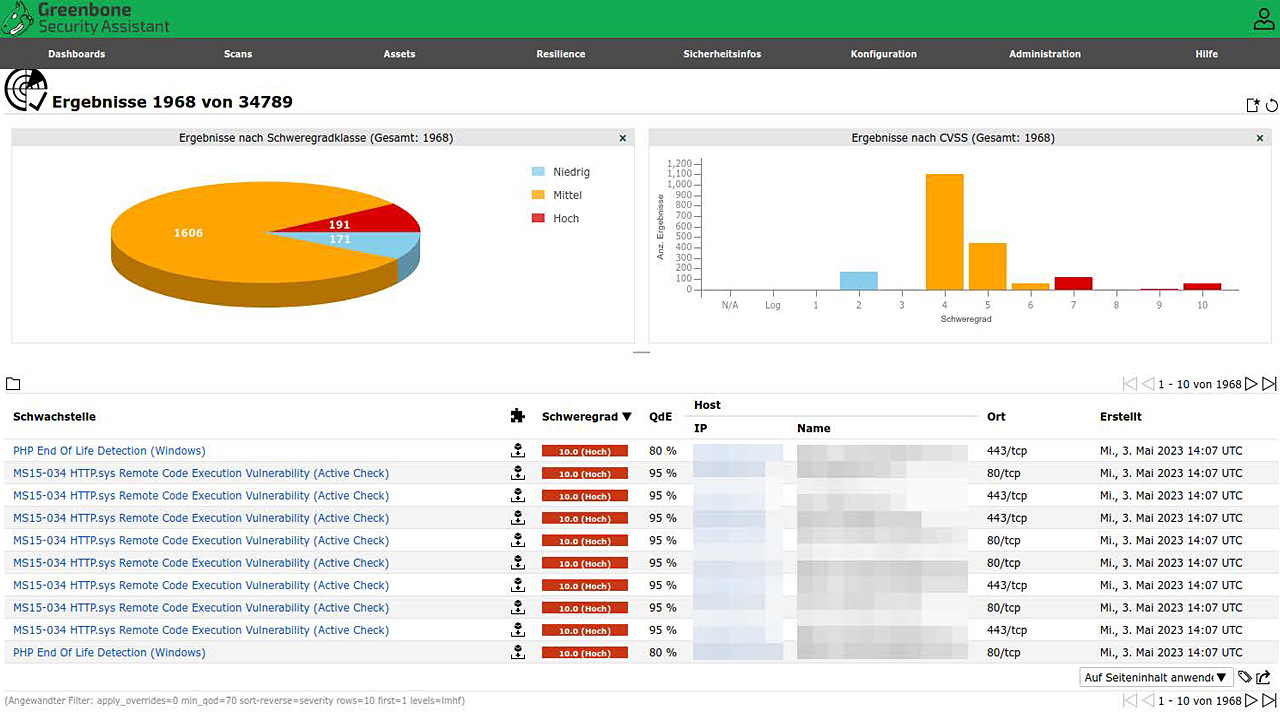
Mit unserer Sicherheitscheck-Dienstleistung auf Basis von Greenbone's OpenVAS bieten wir umfassende Netzwerksicherheitsanalysen an. Wir scannen Ihre Infrastruktur auf Schwachstellen und liefern Ihnen detaillierte Berichte mit klaren Handlungsempfehlungen.
OpenVAS ist eine der führenden Open-Source-Lösungen für Schwachstellenscans und wird weltweit eingesetzt, um Sicherheitslücken zu identifizieren und die IT-Sicherheit zu verbessern. Unsere Dienstleistungen umfassen:
- Umfassende Netzwerkscans: Wir setzen OpenVAS ein, um Ihre IT-Systeme auf bekannte Schwachstellen zu prüfen. Dabei werden sowohl interne als auch externe Netzwerke gründlich untersucht.
- Patch-Audits: Durch die Überprüfung der Aktualität von Software und Betriebssystemen decken wir potenzielle Sicherheitslücken auf und bieten Vorschläge zur Behebung.
- Detaillierte Berichterstattung: Nach dem Scan erstellen wir einen ausführlichen Bericht, der die gefundenen Schwachstellen erklärt und Prioritäten für deren Behebung setzt.
- Handlungsempfehlungen: Neben der Analyse der Schwachstellen bieten wir klare Empfehlungen zur Verbesserung Ihrer Sicherheitsinfrastruktur, einschließlich Patches, Konfigurationsänderungen und weiterer Sicherheitsmaßnahmen.
- Active Directory Sicherheit: Für Unternehmen, die Active Directory nutzen, bieten wir eine spezielle Analyse und Optimierung an, um Sicherheitsrisiken innerhalb des Verzeichnisdienstes zu minimieren.
Unsere Sicherheitschecks bieten Ihnen nicht nur Transparenz über potenzielle Schwachstellen, sondern auch gezielte Maßnahmen, um die IT-Sicherheit in Ihrem Unternehmen nachhaltig zu verbessern.
