PowerShell-Skripte signieren
In der Welt der Windows-Domänensicherheit ist das Signieren von PowerShell-Skripten unerlässlich, um sicherzustellen, dass nur autorisierte Skripte ausgeführt werden. Mit der zunehmenden Nutzung von Skripten aus verschiedenen Quellen wird es immer wichtiger, die Authentizität und Integrität dieser Skripte zu überprüfen. Das Signieren von PowerShell-Skripten und die Konfiguration einer Gruppenrichtlinie, die nur signierte Skripte zulässt, sind wesentliche Schritte zum Schutz der IT-Umgebung. In diesem Leitfaden gehen wir Schritt für Schritt durch die Erstellung eines geeigneten Zertifikats, das Signieren eines PowerShell-Skripts, die Überprüfung seiner Signatur und die Einrichtung eines Gruppenrichtlinienobjekts (GPO), um die Ausführung nur signierter Skripte auf allen Clients und Servern zu erzwingen.
Inhaltsverzeichnis
Selbstsigniertes-Zertifikat erstellen
Öffnen der PowerShell mit Administratorrechten und ausführen des folgenden Befehls:
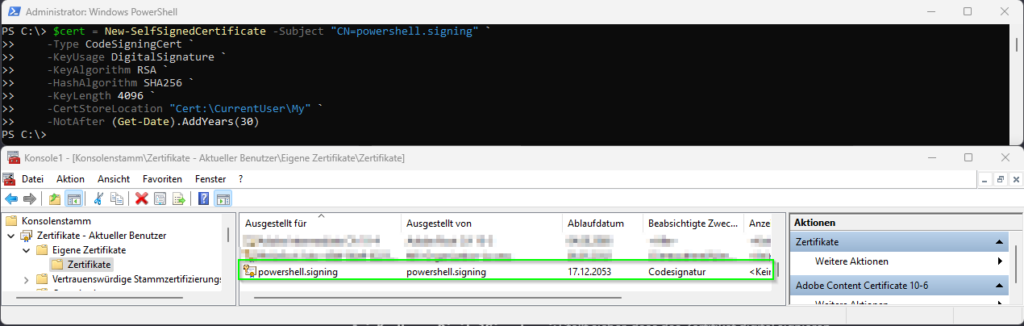
$cert = New-SelfSignedCertificate -Subject "CN=powershell.signing" `
-Type CodeSigningCert `
-KeyUsage DigitalSignature `
-KeyAlgorithm RSA `
-HashAlgorithm SHA256 `
-KeyLength 4096 `
-CertStoreLocation "Cert:\CurrentUser\My" `
-NotAfter (Get-Date).AddYears(30)
Signieren eines PowerShell-Skripts
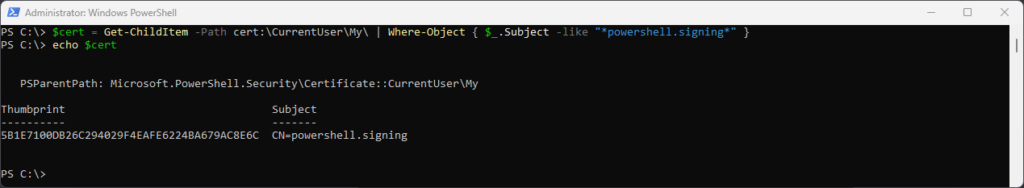
Laden des gerade erstellten Zertifikates in eine Variable:
$cert = Get-ChildItem -Path cert:\CurrentUser\My\ | Where-Object { $_.Subject -like "*powershell.signing*" }
Signieren eines PowerShell-Skripts
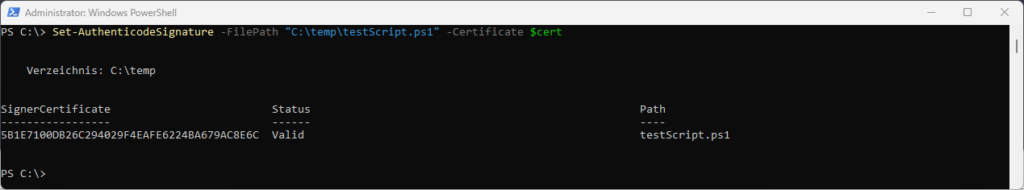
Signieren des PowerShell-Skripts mit folgendem Befehl:
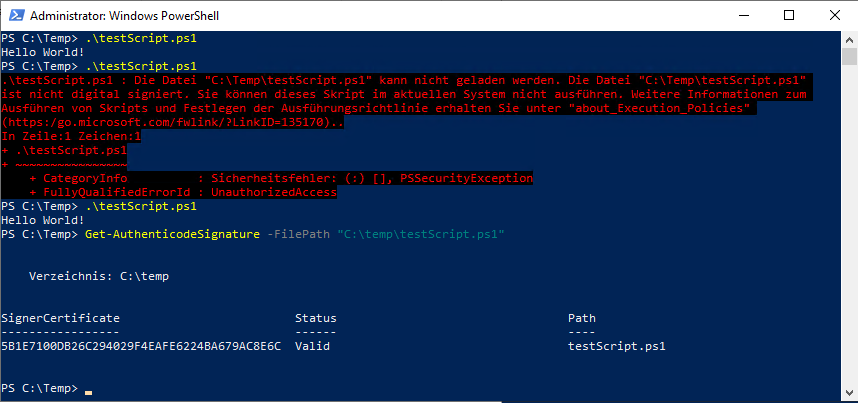
Set-AuthenticodeSignature -FilePath "C:\temp\testScript.ps1" -Certificate $cert
Überprüfen der Signatur
Verwendung von Get-AuthenticodeSignature zur Überprüfung der Signatur des Skripts:
Get-AuthenticodeSignature -FilePath "C:\temp\testScript.ps1"
Erstellung eines GPO zur Ausführung nur signierter Skripte
Erstellung und Bearbeitung eines GPO
- Navigieren zur entsprechenden OU und erstellen eines neuen GPO.
- Klicken mit der rechten Maustaste auf die neue GPO und „Bearbeiten“ auswählen.
Konfiguration der Skriptausführungsrichtlinie
- Navigieren zu „Benutzerkonfiguration“ > „Administrative Vorlagen“ > „Windows-Komponenten“ > „Windows PowerShell“
- Aktivieren von „Skriptausführung aktivieren“ und Setzen der Ausführungsrichtlinie auf „Nur signierte Skripte zulassen“.
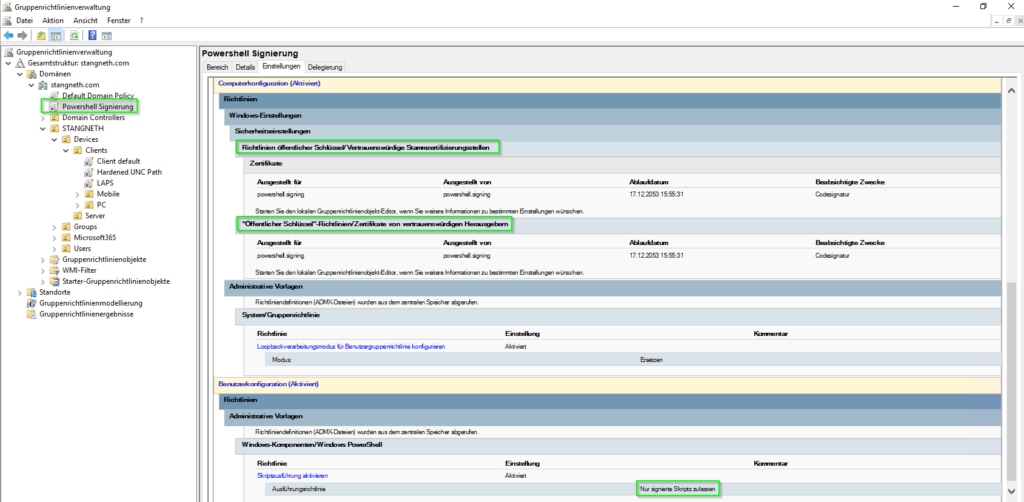
Importieren des Zertifikats in „Vertrauenswürdige Herausgeber“
Damit die Windows-Domäne das selbstsignierte Zertifikat, das zum Signieren von PowerShell-Skripten verwendet wird, vollständig vertraut, ist es entscheidend, das Zertifikat sowohl in die „Vertrauenswürdige Herausgeber“ als auch in die „Vertrauenswürdige Stammzertifizierungsstellen“-Speicher in der Gruppenrichtlinie zu importieren.
Im GPO-Editor navigieren zu „Computerkonfiguration“ > „Richtlinien“ > „Windows-Einstellungen“ > „Sicherheitseinstellungen“ > „Richtlinien für öffentliche Schlüssel“.
Importieren des Zertifikats in „Vertrauenswürdige Herausgeber“
- Klicken mit der rechten Maustaste auf „Vertrauenswürdige Herausgeber“.
- Wählen von „Importieren“, um den Zertifikatsimport-Assistenten zu öffnen.
- Folgen des Assistenten, um das zuvor erstellte selbstsignierte Zertifikat zu importieren.
- Sicherstellen, dass das Zertifikat in der Liste der vertrauenswürdigen Herausgeber erscheint.
Importieren des Zertifikats in „Vertrauenswürdige Stammzertifizierungsstellen“
- Navigieren zurück zu „Richtlinien für öffentliche Schlüssel“.
- Klicken mit der rechten Maustaste auf „Vertrauenswürdige Stammzertifizierungsstellen“.
- Wählen von „Importieren“, um den Zertifikatsimport-Assistenten zu starten.
- Folgen den Anweisungen des Assistenten, um das selbstsignierte Zertifikat zu importieren.
- Bestätigen, dass das Zertifikat nun unter „Vertrauenswürdige Stammzertifizierungsstellen“ aufgeführt ist.
Fazit
Durch das Befolgen dieser Schritte kann die Sicherheit der Windows-Domäne erheblich gestärkt werden. Das Sicherstellen, dass nur signierte PowerShell-Skripte ausgeführt werden, trägt dazu bei, das Risiko der Ausführung unautorisierter oder bösartiger Codes zu minimieren. Die Aufrechterhaltung einer sicheren Umgebung ist ein kontinuierlicher Prozess, bei dem regelmäßige Updates und Wachsamkeit unerlässlich sind.


Keine Kommentare zu PowerShell-Skripte signieren